Unexpected ICMP packets in mirror capture
Hi all. I wonder if anyone can help me with this?
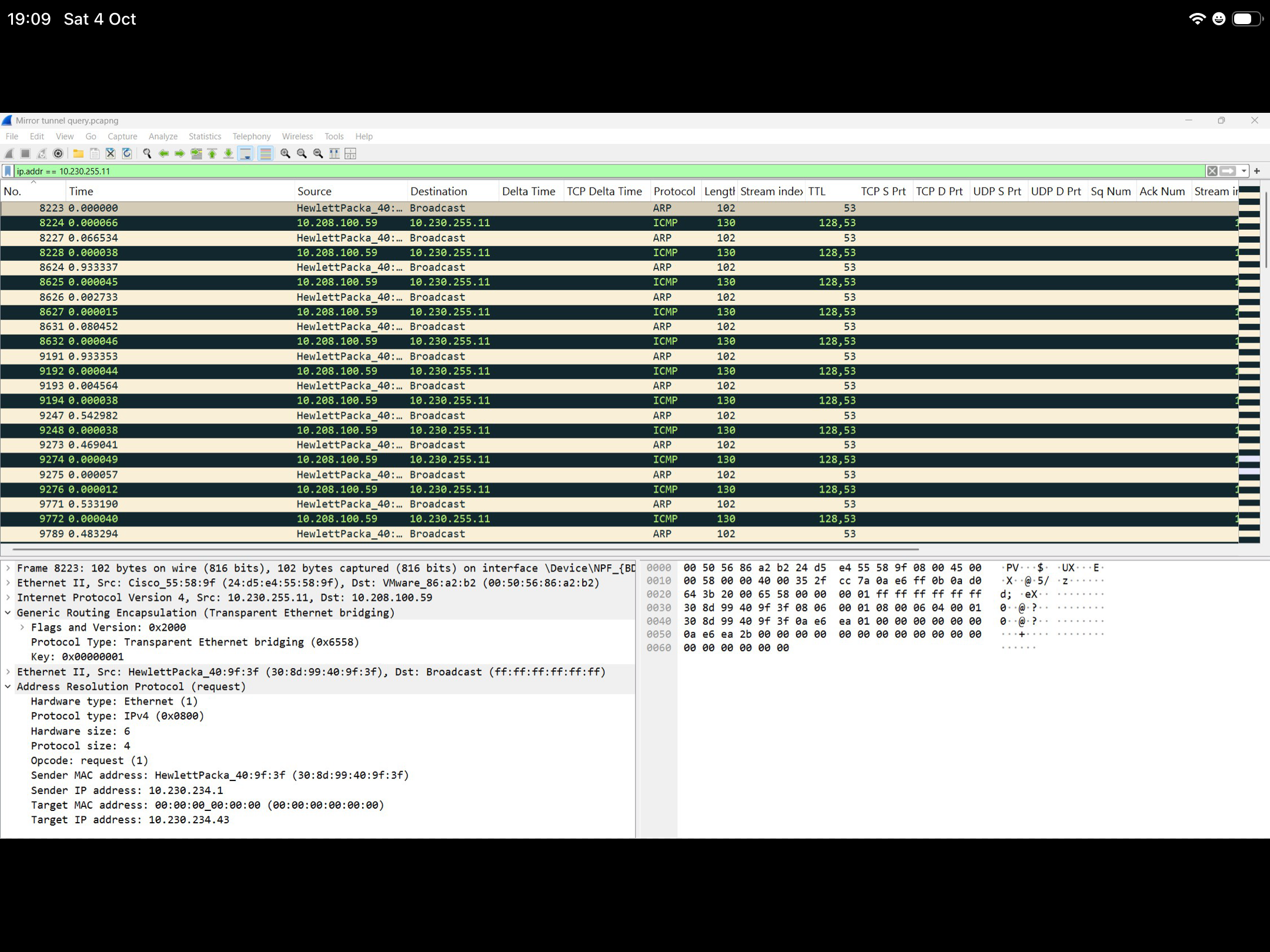
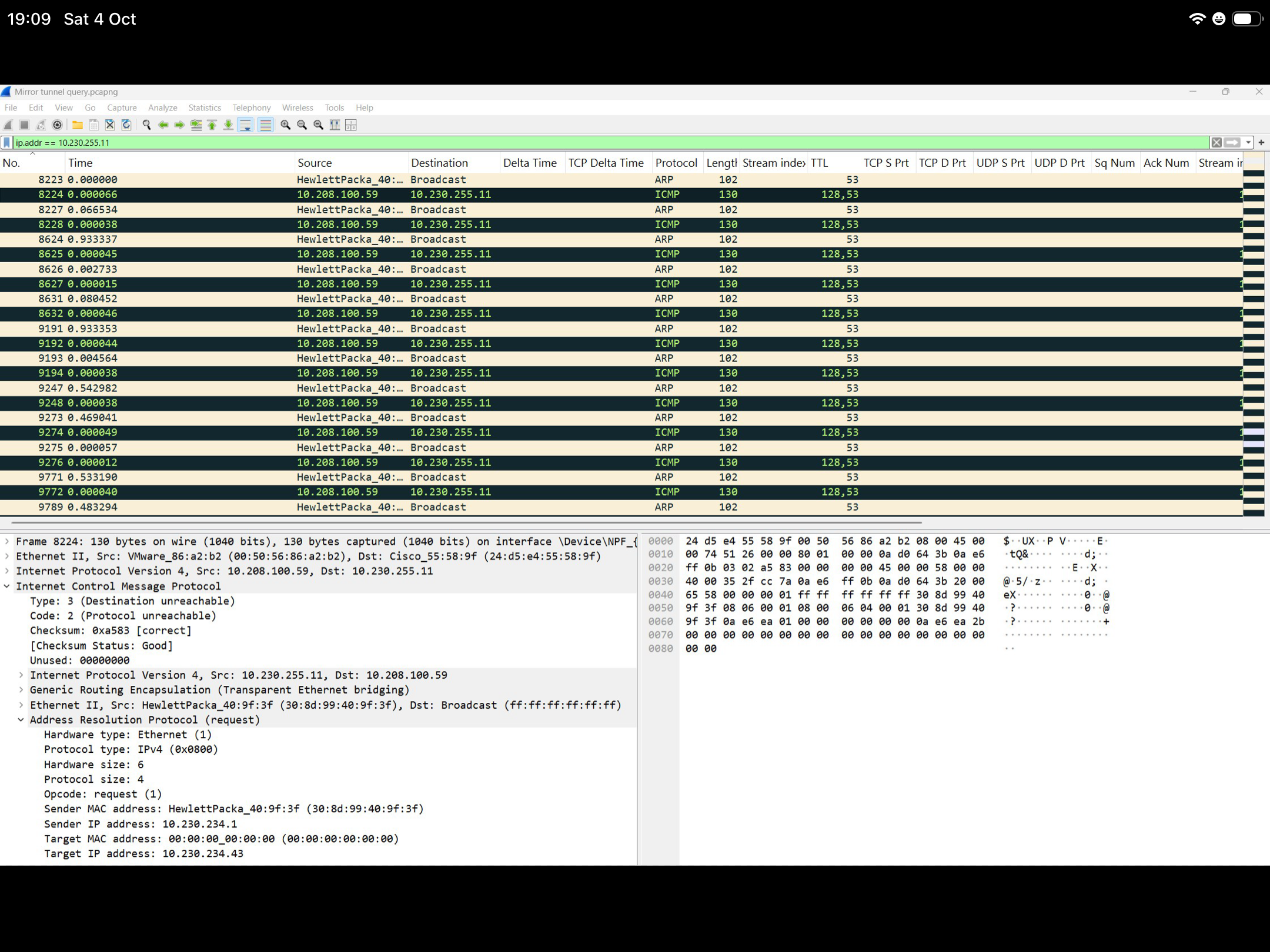
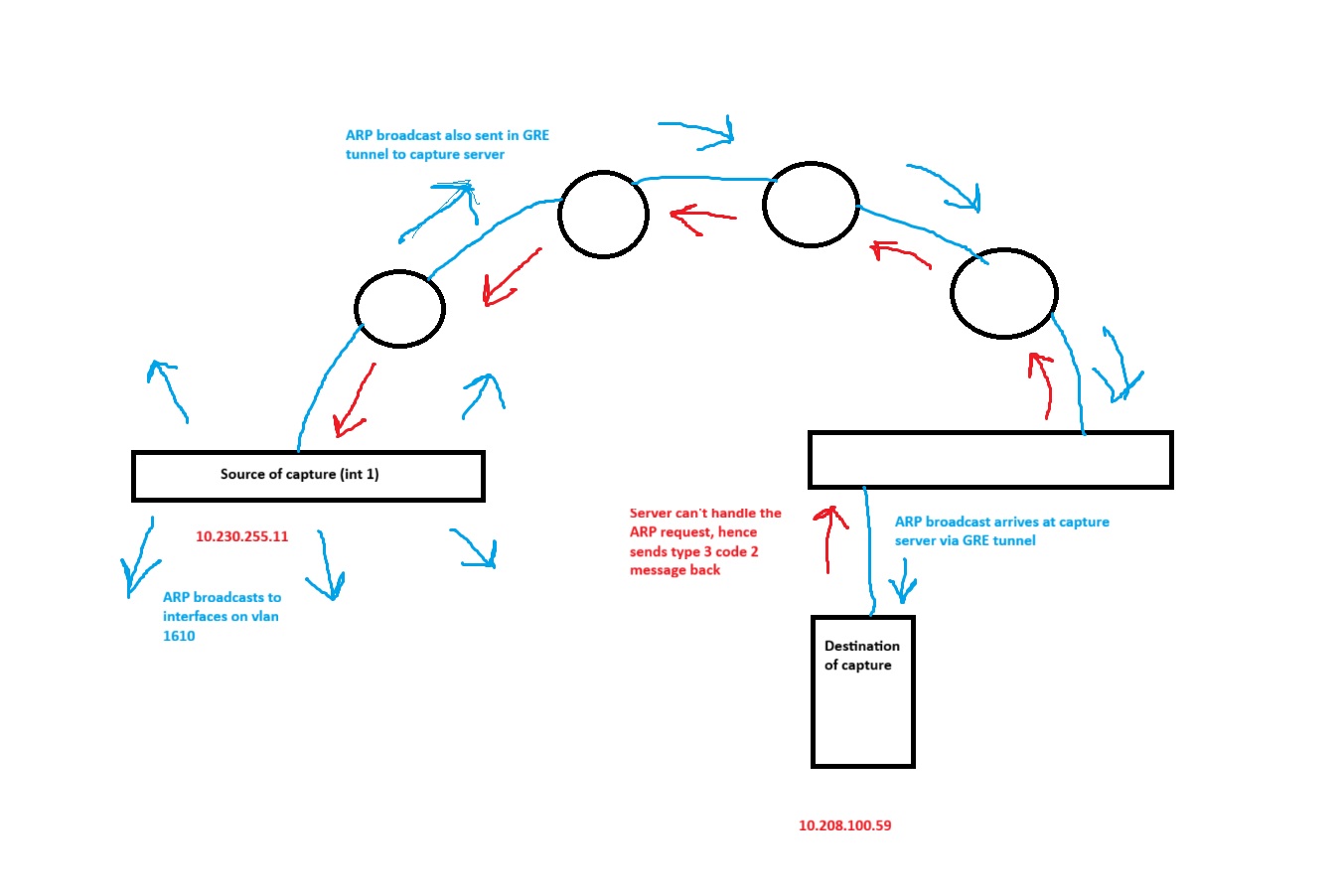
I’m performing a remote packet capture of interface 1 (vlan 1610) of an Aruba 6200F switch with mgmt IP address of 10.230.255.11. I've used the mirror tunnel option to send the data to an off-site server running wireshark (10.230.100.59) using a GRE tunnel. On the server I then filter packets to include only those containing the IP address 10.230.255.11.
I’m comfortable with the ARP information in the pack, but my confusion is that I don't understand how/why the ICMP packets are present. I can clearly see the conversation is between the switch and the capturing server, so my assumption is that it's the mirror data being sent (but that's just a guess).
Thank you very much