Windows Server DNS response cut short
Hi
Looks like our internal DNS servers (W2019) are robbing clients of 257 bytes in DNS traffic. As a result, clients can't get to some of the websites where DNS answers exceed 176 bytes.
Is there a Windows server setting that limits DNS traffic to 176 bytes? We are not seeing this 176 bytes limit on other protocols.
Thank you!


Are you sure it is truncated, there could be reassembly of IP fragments at work? Also, is the "truncated" flag set in the response? If so, it is the duty of the client to re-request the DNS entry, but now over TCP to get the full response.
Are you able to share the pcap for closer inspection?
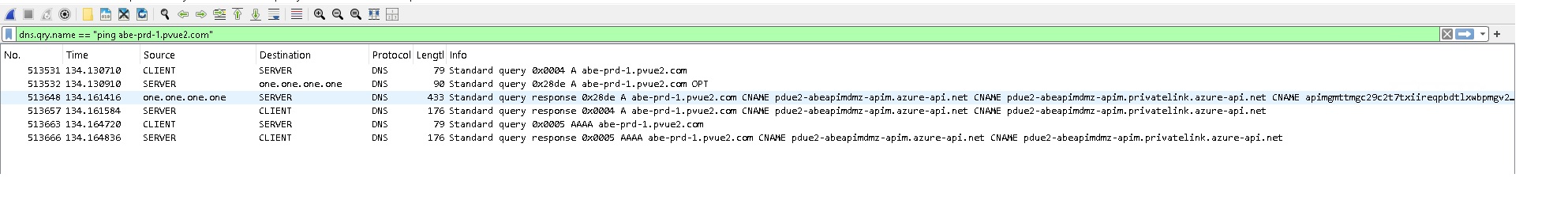
Here is a pcap from a good working environment. Server (192.168.20.5) gets a 433 byte response from 1.1.1.1 and responds to the client with a 422 byte packet.
https://drive.google.com/file/d/1TYma...
Working on getting bad-dns.pacp shared
Capture has been wranglered
97.205.219.232 is 1.1.1.1,
172.16.96.78 - Client, 172.21.59.11 - Server
https://drive.google.com/file/d/1fYz8...
@SYN-bit,
No, Truncated flag is 0. = : Message is not truncated
Someone asked for this behavior here -> https://serverfault.com/questions/116...
I don't know how, but my DNS server is doing exactly what was asked on serverfault post
Is this a CNAME chaining issue or CNAME chaining limit configured on the 172.21.59.11 windows server?