On 16278: Unable to dissect UDP msgpack I found:
tshark -r - -T fields -e data udp.port==60003 | xxd -p -r | msgpack2json -c
Decoding a message to JSON needs 3 steps:
- Output the msgpack from Wireshark as
hexdata, which is easy for UDP as
each message will be exactly one
packet. How are the msgpack objects
in your pcap file sent over TCP? Are
they contained in one packet or are
they segmented? And is there just
one message per TCP stream or are
there a sequence of messages? Are
you able to share a pcap or is there
sensitive information in it?
- Transform the hex data back to raw (binary) data with
xxd -p -r - Convert the binary msgpack data to JSON with msgpack2json
- (optional) add a loop around the tshark command to process each message separately
So IMHO the biggest challenge is not converting to JSON, it's extracting each message out of the TCP stream(s) in your pcap file. It might be easy (if each msgpack message is one TCP segment) or can be hard (if there is a continuous stream of msgpack messages). That all depends on the way the messages are sent in your case.


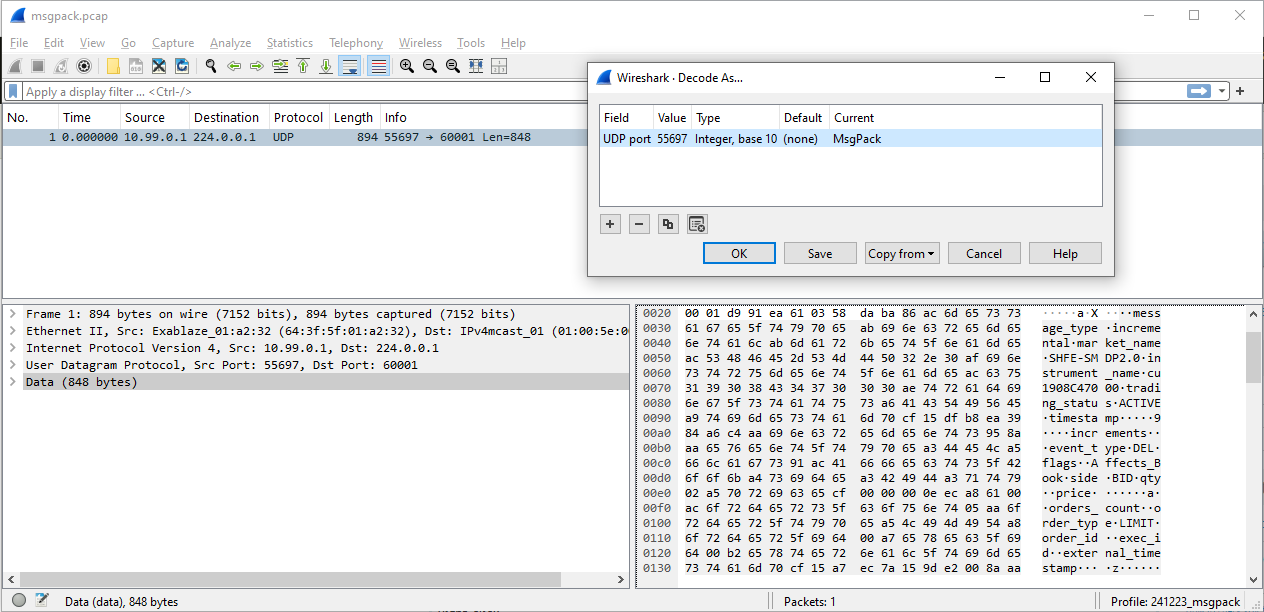
Looks like the
msgpackdissector was meant to be called from thedxldissector.Any chance your captures include
dxldata?https://gitlab.com/wireshark/wireshar...