DNSSEC question
Hi,
We are using DNSSEC on the internal network (Windows 2022 DNS server / 172.16.4.10). Recently I came across a chrome extension from https://dnssec.uz and added it to my browser.
When accessing phl-esxi1 the extension confirms that DNSSEC is enabled and working correctly, but if i look at DNS traffic in Wireshark, nothing in the DNS answer options has any indication of DNSSEC being present.
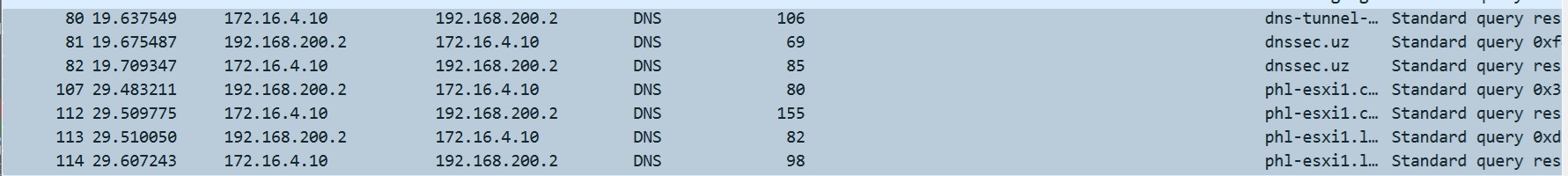
Does DNSSEC use something other than DNS protocol to check the authenticity of the record?
Thanks
Edit:
Seeing DNSSEC fields after getting GPO applied to the computer object
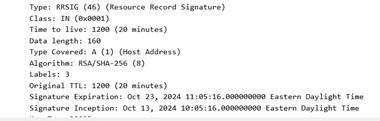

What is the full domain for
phl-esxi1? (The column is truncated in the Wireshark screenshot)it's ourdomain.local
truncated to hide the identity
Have you looked at this presentation: dnssec.uz: Protect your website
Is the browser extension using
dnsviz probe?the chrome extension is irrelevant, i only mentioned it to show that DNSSEC is enabled.
I may have figured it out, AD team blocked the inheritance on the GPO with DNSSEC name resolution policy. Once computer object moved out to another OU, the policy applied and I am able to see additional records I was missing earlier.
So Wireshark did not display the data that is not in the capture file?
There are sample captures in Wireshark Gitlab issues - search on "dnssec"