There is a Wireshark tool for making TCP capture filters: String-Matching Capture Filter Generator
With a little math, you can do the same thing for UDP.
(udp port 53) && (udp[10] & 0x80 != 0) && (udp[11] & 0x0f == 0) && udp[20:4] = 0x04687474 && udp[24:4] = 0x70026677 && udp[28:4] = 0x08757064 && udp[32:4] = 0x61746573 && udp[36:4] = 0x31076e65 && udp[40:4] = 0x74676561 && udp[44:4] = 0x7203636f && udp[48:2] = 0x6d00
(udp port 53) - DNS typically responds from port 53
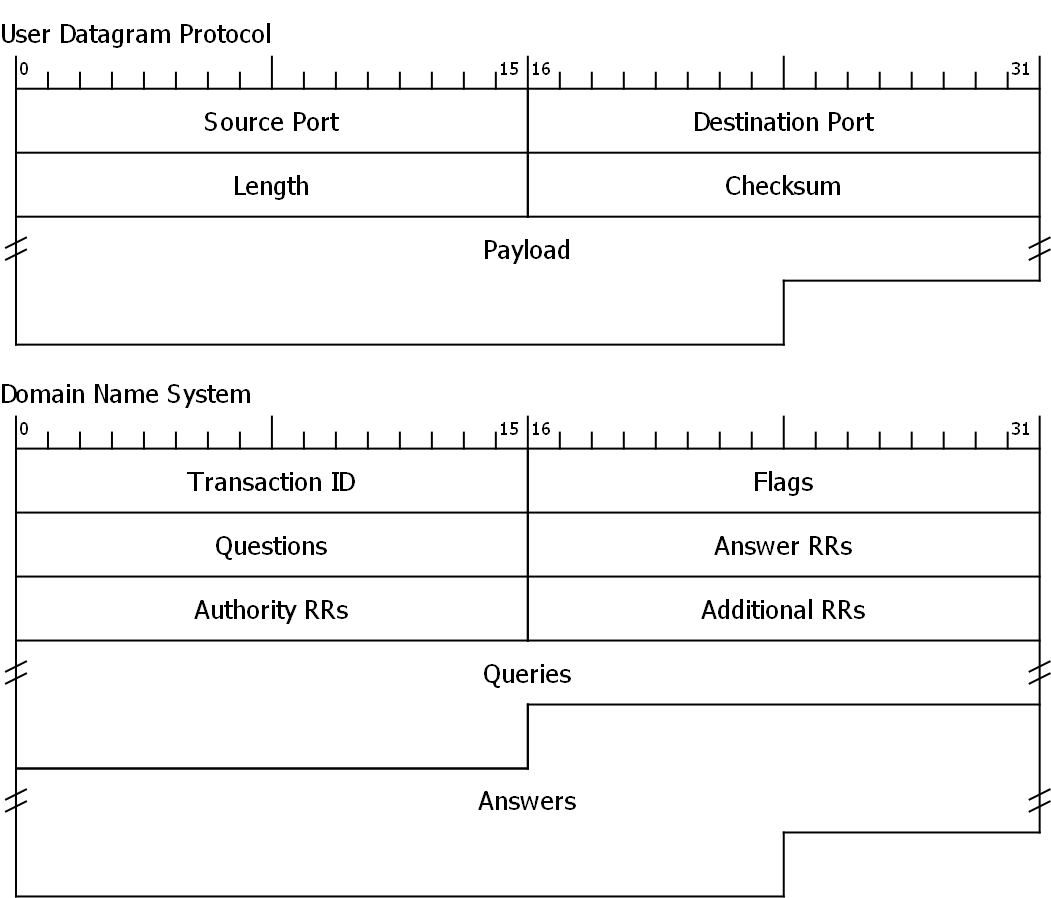
(udp[10] & 0x80 != 0) 8 bytes (0-7) of UDP header + 3rd byte in to UDP data = DNS flags high byte
(udp[11] & 0x0f == 0) 8 bytes (0-7) of UDP header + 4th byte in to UDP data = DNS flags low byte
Look for response with no errors
Flags: 0x8180 Standard query response, No error
1... .... .... .... = Response: Message is a response
.000 0... .... .... = Opcode: Standard query (0)
.... .0.. .... .... = Authoritative: Server is not an authority for domain
.... ..0. .... .... = Truncated: Message is not truncated
.... ...1 .... .... = Recursion desired: Do query recursively
.... .... 1... .... = Recursion available: Server can do recursive queries
.... .... .0.. .... = Z: reserved (0)
.... .... ..0. .... = Answer authenticated: Answer/authority portion was not
authenticated by the server
.... .... ...0 .... = Non-authenticated data: Unacceptable
.... .... .... 0000 = Reply code: No error (0)
RFC 1035 - DOMAIN NAMES - IMPLEMENTATION AND SPECIFICATION
3. DOMAIN NAME SPACE AND RR DEFINITIONS
Domain names in messages are expressed in terms of a sequence of labels.
Each label is represented as a one octet length field followed by that
number of octets. Since every domain name ends with the null label of
the root, a domain name is terminated by a length byte of zero. The
high order two bits of every length octet must be zero, and the
remaining six bits of the length field limit the label to 63 octets or
less.
Queries
http.fw.updates1.netgear.com: type A, class IN
Name: http.fw.updates1.netgear.com
[Name Length: 28]
[Label Count: 5]
Type: A (Host Address) (1)
Class: IN (0x0001)
http.fw.updates1.netgear.com = 0468747470026677087570646174657331076e65746765617203636f6d00
http = Length: 04, Chars: 68 74 74 70
fw = Length: 02, Chars: 66 77
And so on .....
udp[20:4] = 0x04687474 && udp[24:4] = 0x70026677 && udp[28:4] = 0x08757064 && udp[32:4] = 0x61746573 && udp[36:4] = 0x31076e65 && udp[40:4] = 0x74676561 && udp[44:4] = 0x7203636f && udp[48:2] = 0x6d00
Break the Query name returned in the response into 4 byte (and final 2 byte) chunks.
Byte offsets start at 20 = UDP header (8) + DNS header (12) = 20 and go up 4 bytes each comparison.
pcap-filter man page:
proto [ expr : size ]
The byte offset, relative to the indicated protocol layer, is given by expr. Size is optional and indicates the number of bytes in the field of interest; it can be either one, two, or four, and defaults to one.


"Display filter" != "Capture filter"
You want to create a capture filter, not "create a Display filter " ?