The extra info is helpful, I have downloaded the following files from your question; "google search on port 443.pcapng" and "SSLKEYLOG.log".
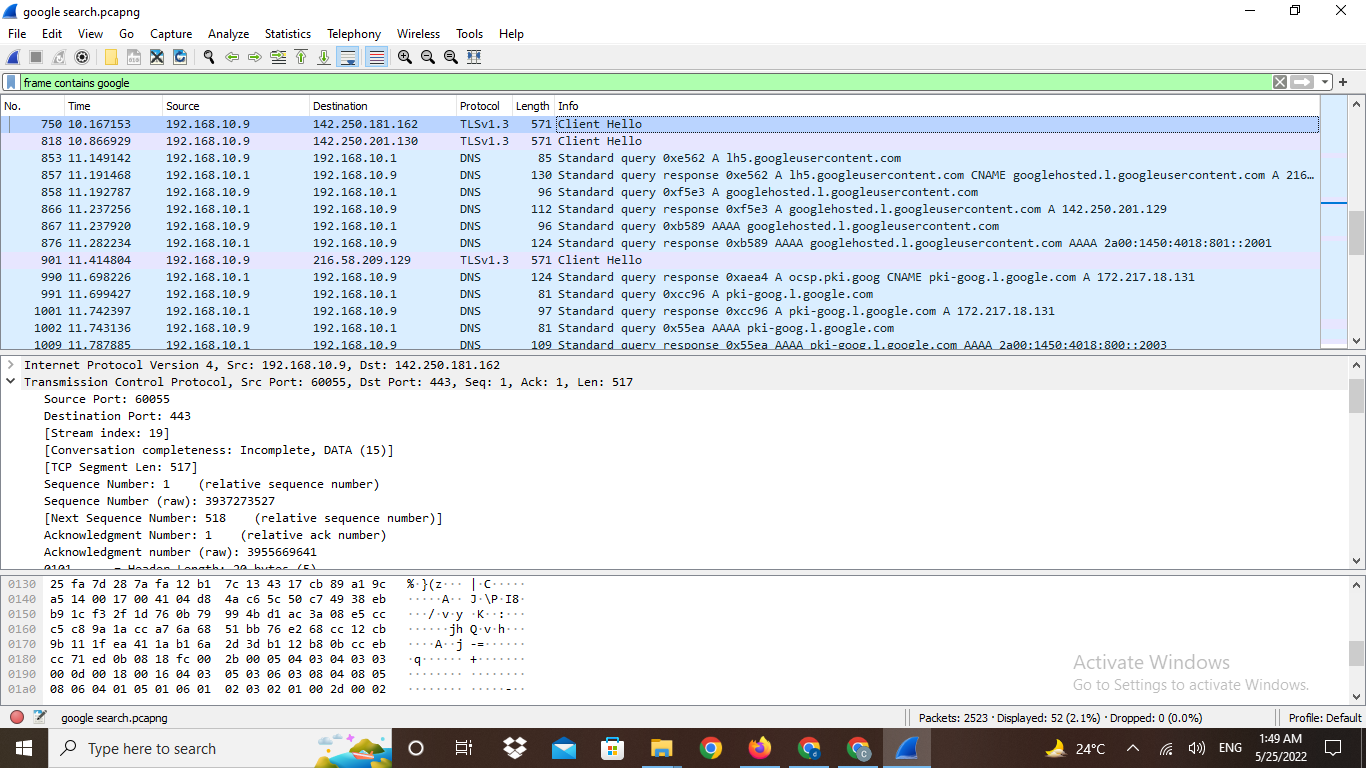
Firstly you have a captured a number of external connections in the traffic, these may have been from applications other than your browser, but they do make finding the google.com connection a bit more difficult. To locate the server that is being used for the connection, I like to add the "Server Name Indication" field as a column. To do this, click on frame 3 in the packet list, then in the packet details pane expand the "Transport Layer Security" header, then the "TLSv1.2 Record Layer: Handshake Protocol: Client Hello" header, then the "Handshake Protocol: Client Hello" header, then the "Extension: server_name (len=25)" header, then the "Server Name Indication extension" header so that you can see the "Server Name: sockets.anty-api.com" field. Right click the field and select "Apply As Column". This then adds the "Server Name" column to the packet list.
Even though this is a simple Google search, there are a lot of bits involved, so to abbreviate this answer, the data you want is in the connection that starts at frame 221
Scroll down the packet list until frame 221. Next, filter the display to show only data from this connection, so right click frame 221 in the packet list and select "Follow -> TCP Stream", as this is a TCP connection. This brings up the TCP stream dialog that shows the TLS handshake for this connection along with some encrypted traffic data. Close the TCP Stream dialog. You should now see that frame 31 in the packet list the server name is "www,google.com" which is your target server.
Next, to decrypt the data, copy the "SSLKEYLOG.log" file into the same place as the capture file. In Wireshark right click frame 231 in the packet list and select "Protocol Preferences -> Transport Layer Security -> (Pre)-Master-Secret log filename:". In the edit field that appears at the top of the packet list, use the browse button to select the "SSLKEYLOG.log" file.
If you have correctly captured the required keying material, then the traffic should decrypt, it does for me and I can now see HTTP2 packets in the list. To simplify things, limit the display of this connection to HTTP2 packets. Select frame 233, then in the packet details, right click one of the "HyperText Transfer Protocol 2" headers and select "Apply As Filter -> ...and Selected". The decrypted HTTP2 traffic now shows what goes on just to bring back the initial Google Search page.
Unfortunately I have now hit a brick wall. I suspect your Google search for "Stima" is now being done via one of the QUIC connections in the capture but I can't get those to decrypt.
Edit: You had changed the search to stearing gulls which confused me.