WLAN Capture Filter on OUI
Been playing for hours now so coming to the experts! I am pretty sure this is really a PCAP question but I can't figure out where to ask that either. Not so smart am i. At any rate been trying to set up a capture filter to gather everything to/from a particular OUI on wifi. The setup - mediatek wifi adapters on linux in monitor mode. Working great.
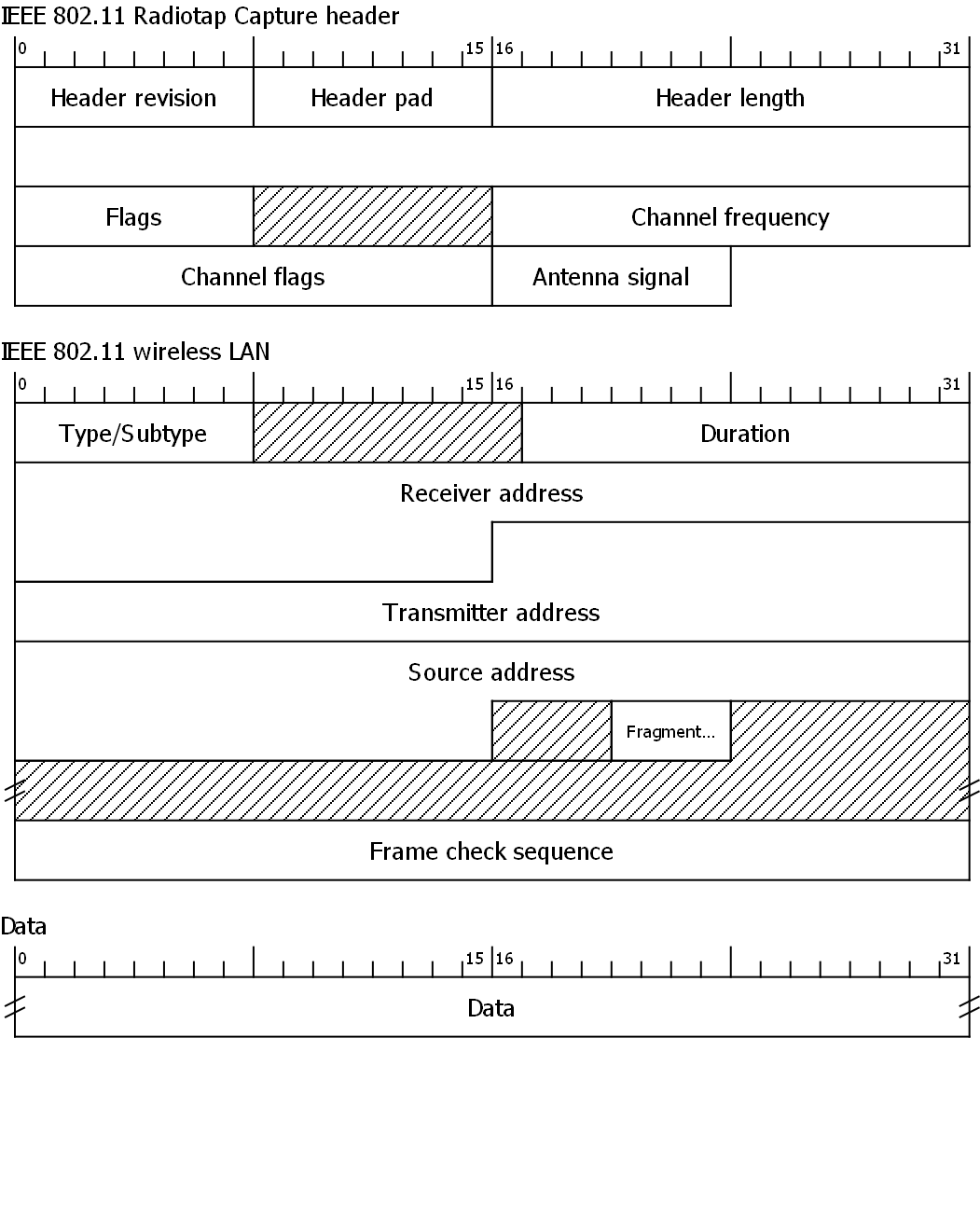
Using slicing I can do anything i want with wlan [0] == 0xnn and get the expected results. However, using any other byte, IE: wlan[1] == 0xnn for instance results in a null capture. Even though I am using nn that I know is byte two of the station. Of course, the more complicated forms don't work either such as wlan [0:2] ==0xnnnn and such.
Wish I had added. Tried with 3.2.15rc0 and v3.4.7rc0-42-ge479ced643a7 compiled natively on RPI also loaded 1.8.1 and 1.10.0 libpcap. Kernel is 5.10.17-v71+

Are you looking for a capture filter (pcap-filter) or a display filter (wireshark-filter) ?
capture filter for sure. need to reduce the clutter on the capture side.
wlan [0] == 0xnnis syntax for a Wireshark display filter.Check the pcap-filter man page for capture filter syntax.
See this previous question for wlan capture filter examples.
Thank you for your answer. I have read the man page many times ... because I miss stuff all the time. It is not helping me to achieve my goal. The syntax I and you reference are shown in various places as pcap syntax. The man page says: Similarly, tr and wlan are aliases for ether;
This shows a valid way to do what I want to do and it works on ethernet link to valid way
Copied here for ease of access. 'ether[0:2] == 0x1122 && ether[2:1] == 0x33 \ || ether[6:2] == 0x1122 && ether[8:1] == 0x33'
So My guess is wlan alias slicing doesn't work correctly? Because I have followed it directly as the man page states.
(wlan[4:2]==0x026a && wlan[6]==0xe3) or (wlan[10:2]==0x026a && wlan[12]==0xe3)There are four (4) bytes before the addresses start. Capture filter above matched
02:6a:e3