STEAMDISCOVER (steam_ihs_discovery)
Hey there,
was checking my gaming-traffic lately with wireshark: Running Steam on Ubuntu 18.04. using OpenVPN.
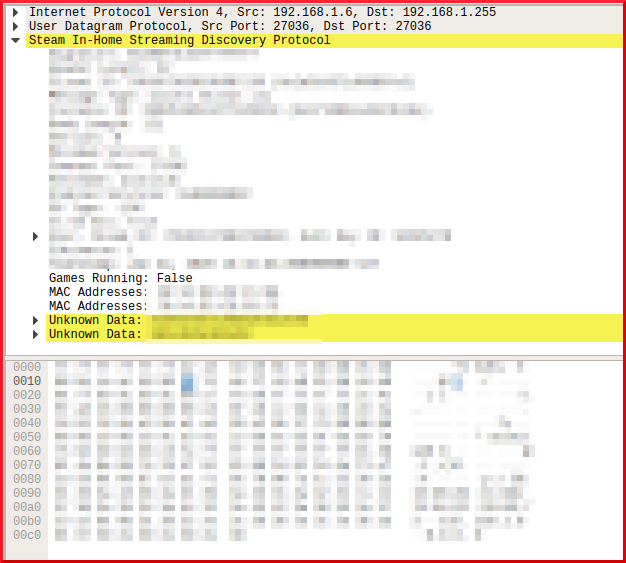
First thing I discoverd was that STEAMDISCOVER-protocol was send to broadcast (local). It contains some information about the computer used and the Steam-account.
Nothing unusual so far, but as I looked deeper into the packets I found that it would pull the MAC-adress of an interface which I previously manually took down via ifconfig (eth0).
Second thing: It pulled the original MAC-adress of my wlan0-interface which I was using and this MAC-adress was spoofed.
How does it do that? It seems that steam pulls these information directly from the chips, ignoring/bypassing the settings of the OS:
(Wanted to attach screenshots, but I'm not allowed until I have 60 points, lulz...)
Screenshots added:

Post screenshots, or even better captures, to a public file share, e.g. Google Drive, DropBox etc. and post a link to the item(s) back here.
added screenshots to the original post. Everybody running Steam can check themselves. No program I ever saw pulled original MAC's from interfaces that were down or spoofed, I'm into that for years now, never saw that. I think it's because Steam writes stuff into the MBR, but I can be wrong here. It's an absolute rootkit-like program if you ask me.. Anybody else?