 | 1 | initial version |
The TCP payload of NDM packets doesn't start with a SSL record.
C:D adds a 20 byte header in front of the SSL records.
This is why wireshark cannot dissect the SSL record at offset 0 after the TCP header.
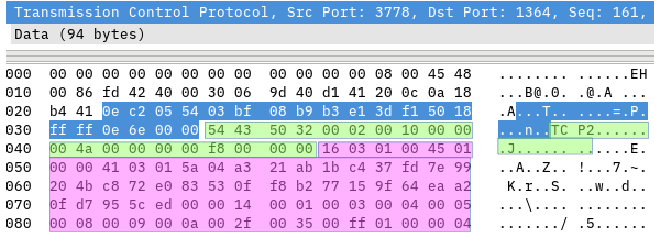
Regards Matthias
 | 2 | No.2 Revision |
The TCP payload of NDM packets doesn't start with a SSL record.
C:D adds a 20 byte header in front of the SSL records.
This is why wireshark cannot dissect the SSL record at offset 0 after the TCP header.

Regards Matthias In this case the session is using TLS1.0
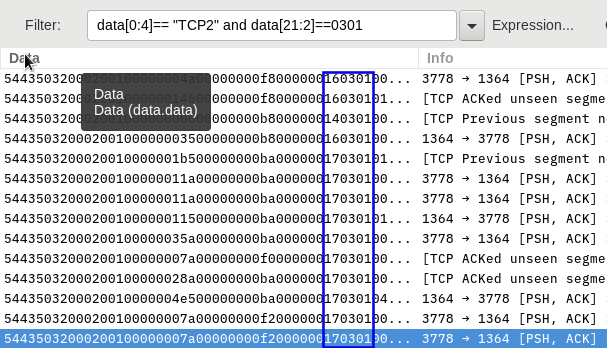
If you are interested in the SSL/TLS Version being used only you can create a coloring rule to give you a hint.
@C:D TLS1.2@data[0:4]== "TCP2" and data[21:2]==0303@[56198,46230,57775][0,0,0]
@C:D TLS1.1@data[0:4]== "TCP2" and data[21:2]==0302@[56198,46230,57775][0,0,0]
@C:D TLS1.0@data[0:4]== "TCP2" and data[21:2]==0301@[56198,46230,57775][0,0,0]
@C:D SSL_V3@data[0:4]== "TCP2" and data[21:2]==0300@[56198,46230,57775][0,0,0]
Regards Matthias