Hi; On Tshark; I am trying to run this command "tshark -r /root/Desktop/a.pcap -T fields -e "dns.count.answers>3"" however I always see; " (process:2009): WARNING : 'dns.count.answers>3' isn't a valid field! tshark: Some fields aren't valid" Do you have any idea about how can I see "dns.count.answers>3" on tshark and then output it as a cvs. file. Thank you very much. asked 27 Jul '17, 05:43 alfrego129 edited 27 Jul '17, 05:45 |
2 Answers:
I think you aren't using -e correctly. If you look for a field having certain values, use a filter (with "-Y"), and -e without the operator, like this: answered 27 Jul '17, 05:52 Jasper ♦♦ |
You have mixed together two things - a display filter and list of fields. The correct way to achieve your goal would be to write
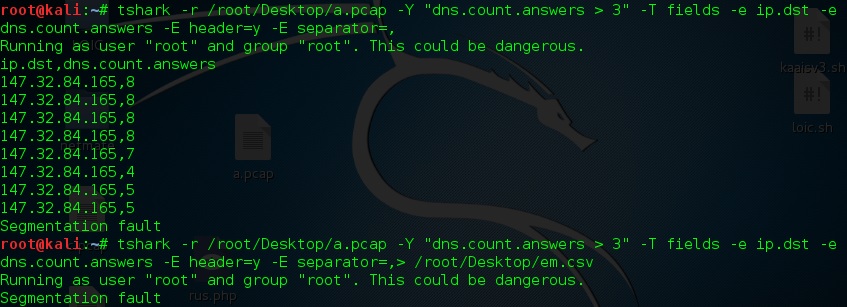
answered 27 Jul '17, 05:59 sindy Thank you very much, it works very well, in addition; I am trying to extract it csv file format and I used "tshark -r /root/Desktop/a.pcap -T fields -e dns.count.answers -e ip.dst -Y "dns.count.answers > 3" header=y -E separator=, >/root/Desktop/x.csv" However, it did not work, do you have any idea? (27 Jul '17, 20:20) alfrego129 How exactly it "did not work"? What is your goal? The way you've done it, (27 Jul '17, 23:20) sindy I am trying to extract dns.count.answers and ip.dst as a csv file then I will implement it in Weka machine learning software. In this command "tshark -r /root/Desktop/a.pcap -T fields -e dns.count.answers -e ip.dst -Y "dns.count.answers > 3" I can see packets, it is ok. However, in this command "tshark -r /root/Desktop/a.pcap -T fields -e dns.count.answers -e ip.dst -Y "dns.count.answers > 3" header=y -E separator=, >/root/Desktop/x.csv" it saves on Deskto, it is ok but the file is empty... (28 Jul '17, 04:20) alfrego129 First, I'd recommend to always tune the command line parameters without the Second, if you have copy-pasted your command line here, a (28 Jul '17, 04:36) sindy Maybe you don't have permission to write to (28 Jul '17, 04:43) cmaynard ♦♦ I really confused because when I try "tshark -r /root/Desktop/a.pcap -T fields -e ip.dst -E header=y -E separator=, >/root/Desktop/em.csv" it saves successfully and I can see ip numbers. It is ok. So according to this part I have a permission to write root/Desktop. However, when I try "tshark -r /root/Desktop/a.pcap -T fields -e dns.count.answers -Y "dns.count.answers > 3" -E header=y -E separator=, >/root/Desktop/em.csv" with missing E, the file is saved but it is empty. Also as you said without "> /root/Desktop/x.csv" it works and I can see the numbers. So there is a problem in the second paragraph but I could not figure out from last night to this morning, if you have any idea please let me know :) Thank you very much again (28 Jul '17, 05:05) alfrego129
I'm lost here. No When you successfully test the complete command If the file is still empty after that, can you delete it and try again? I could imagine the file being owned by another user or open for writing by another application, but I would expect bash to issue an error message in either of these cases. (28 Jul '17, 05:35) sindy
When I checked em.csv with using nano or any text format it is empty... (28 Jul '17, 06:43) alfrego129 Well... how comes you are not scared by the (28 Jul '17, 06:47) sindy I received Segmentation fault message "tshark -r /root/Desktop/a.pcap -T fields -e ip.dst -E header=y -E separator=, >/root/Desktop/em.csv" it saves successfully and I can see ip numbers. It was ok, therefore, I did not consider it deeply. Do you have any idea how can I fix it? Thank you. (28 Jul '17, 07:22) alfrego129 I would assume that the difference is the number of packets processed until the crash happens. When you do not display-filter the packets, much more lines (actually, all) make it to the output, so the buffer is flushed at least once before the crash and thus the file is not empty. With the display filter in place, so few lines get to the buffer before the crash that no flush takes place so the file remains empty. What I would do on your place would be to run tshark with no display filter and with add This behaviour is usually caused by a bug in a dissector of some protocol, causing it to crash on an illegal (or even legal) field value of that protocol. So you would then use Now you have two possibilities - the suspicious packet is interesting for you because it is a DNS response, or it is not (remember I don't know whether your input file only contains DNS responses, or the complete traffic on the interface, or something in between these two extremities). If none of the two suspicious packets is a DNS response, you can use
(You cannot use What to do further depends on the Wireshark version you use:
Or you can publish the file with the killer packet, login-free, on some common file-sharing service and put a link to it here. (28 Jul '17, 08:28) sindy If you only run (28 Jul '17, 08:30) cmaynard ♦♦ Thank you very much for answers, I ll try all of them tomorrow and let you know. (28 Jul '17, 14:13) alfrego129 showing 5 of 13 show 8 more comments |

Thank you very much, it works very well, in addition; I am trying to extract it csv file format and I used "tshark -r /root/Desktop/a.pcap -T fields -e dns.count.answers -e ip.dst -Y "dns.count.answers > 3" header=y -E separator=, >/root/Desktop/x.csv"
However, it did not work, do you have any idea?