When using display filter -Y "http" in tshark, I can only see HTTP request packet is recognized. But I can see more packets are decoded as HTTP, including HTTP response. Any idea why?Output from tshark with display filter output from tshark without display filter asked 04 Jun '17, 22:12 tong1125 edited 05 Jun '17, 02:17 grahamb ♦ |
3 Answers:
It turns out I made a silly mistake. I disable "allow subdissector to reassemble TCP streams" on Windows, but I forgot the do the same thing on Linux host. Btw, wireshark preference file locates at ~/.config/wireshark If you are not able to find the preference file, you can use tshark -o top.desegment_tcp_stream to disable it answered 29 Jun '17, 02:00 tong1125 |
The display filter All the other packets have been dissected as TCP as they either don't contain any HTTP data, or are fragments of an HTTP message and only the final packet that completes the HTTP response will be dissected as HTTP and show up with an HTTP display filter. answered 05 Jun '17, 02:24 grahamb ♦ showing 5 of 9 show 4 more comments |
Are you possibly forgetting to input the profile in tshark? If your using a specific profile in the GUI where you have the TCP settings to allow you to see HTTP, make sure to specify that same profile in tshark, else it will use the default like below. tshark -r test.pcap -Y http.response -Tfields -e frame.number -e http.response.code -e http.time -C tcp-tshoot C:\ tshark -r 90_streams.pcap -Y http.response -Tfields -e frame.number -e http.response.code -e http.time -C tcp-tshoot 5 200 0.025068000 49 200 0.022251000 55 200 0.194137000 75 200 0.243763000 103 200 0.250902000 132 200 0.029903000 142 200 0.039818000 answered 03 Jul '17, 15:24 Sneak2k2 |

Thanks for the feedback. My concern is wireshark GUI can recognize those TCP segments as HTTP, but tshark CLI could not.
How can I get the filtered output like GUI in tshark?
Try adding
-2to the tshark command line.-2 is already included, it doesnt work.
Can you share a capture in a publicly accessible spot, e.g. CloudShark, Google Drive, DopBox etc?
Here comes the pcap, thanks
https://drive.google.com/file/d/0B3Lqaled8eVCZlg1cXNYOU1FeGc/view?usp=sharing
What version of Wireshark and tshark are you using?
Tshark version is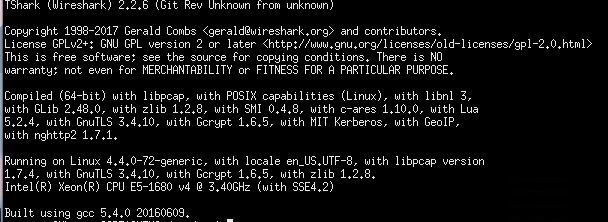
And wireshark GUI version is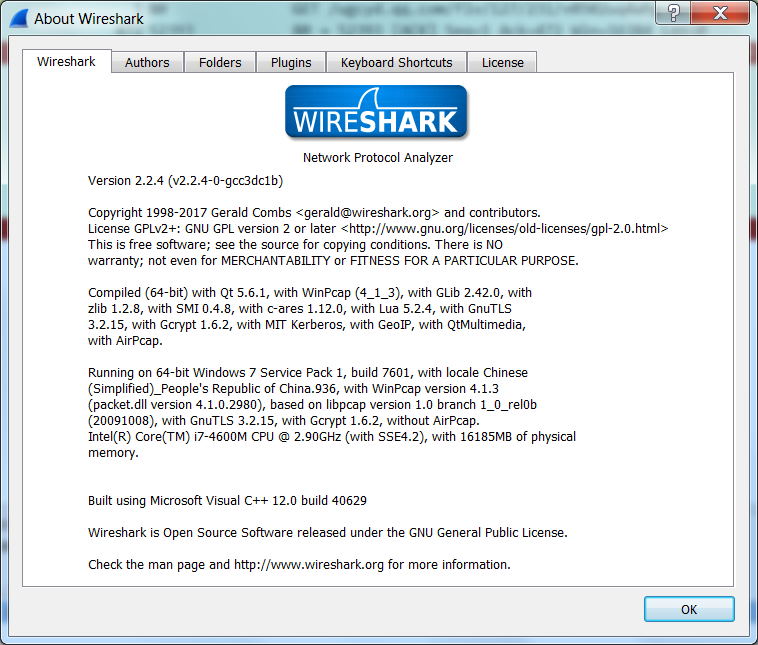
Upgrade the wireshark to 2.2.6 on Windows, it is still working.maybe only Linux has problem?
So tshark on Windows works for you?