This is a followup question from an earlier post whihc was answered by SYN-bit: I just realized something that does not make sense to me in the capture: Wireshark and the program I am using to perform the nttcp test (nttcp under Cygwin) are executed on the same machine: how is it possible that Wireshark captures all packets, but my nttcp program misses them? Or am I misinterpreting the results here? The capture is located here. Thanks! Dirk asked 18 Feb '15, 13:03 djbuijs |
One Answer:
"... how is it possible that Wireshark captures all packets, but my nttcp program misses them?"
" but there's still the issue of the Duplicate ACKS, which suggests that somewhere in a lower layer packets got dropped. However, Wireshark seems to have managed to capture all packets!" Well, this trace does not contain all packets that were actually flowing as dumpcap couldn't keep up with the amount of traffic. And, the packets are not necessarily 'dropped in the lower layer'. In your case the packets are dropped in the TCP layer of Windows7 because the TCP checksum is incorrect in packets that caused the duplicate ACKs. _ws.expert.severity gt "warn" will yield those packets if you enable TCP checksum validation in the protocol preferences.
answered 21 Feb '15, 02:41 mrEEde edited 22 Feb '15, 02:20 |

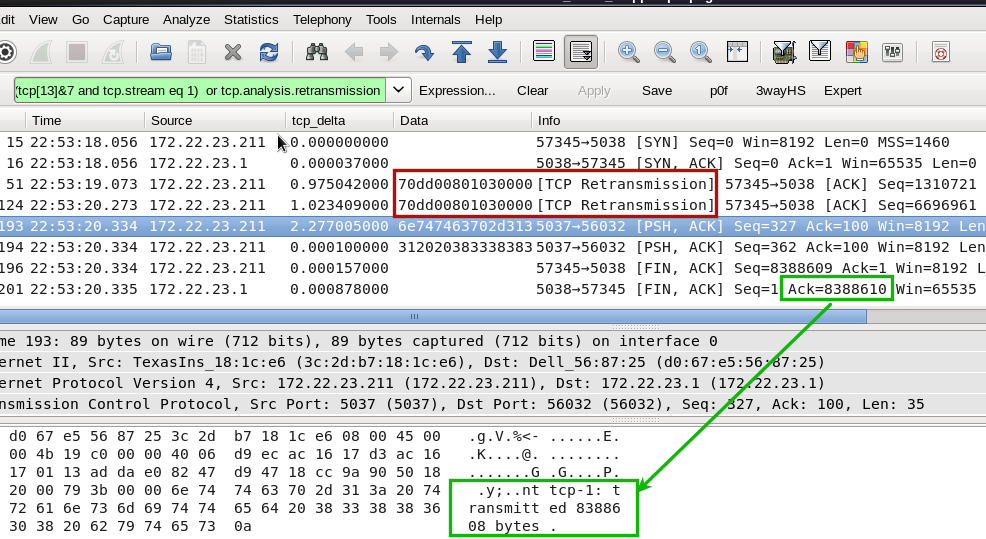
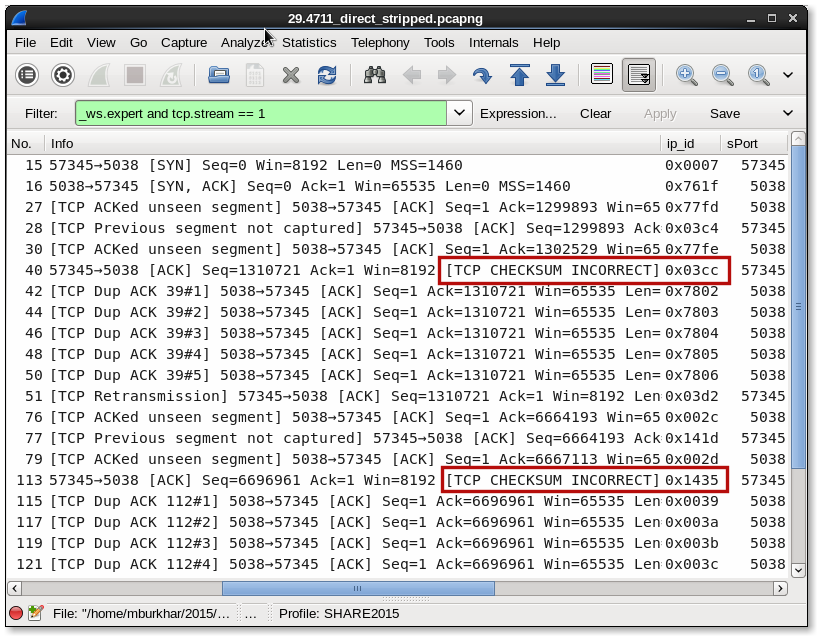
Hi Matthias, Thanks for your help on this. It's still a bit of a mystery what is going on exactly. I understand the way TCP is basically a pipe when seem from the application layer, but there's still the issue of the Duplicate ACKS, which suggests that somewhere in a lower layer packets got dropped. However, Wireshark seems to have managed to capture all packets!
Regards, Dirk