Hello. I have a great problem using tshark. A have a pcap file with SSL certificate. After pressing «Decode as -> Certificate » in Wireshark i see something like picture below. Every field have its real name.
But when im trying to open and decode this cert file in tshark – a see something like the next picture – fields are decoded correctly, but I don`t see field names – subjectPublicKey e.t.c! I start tshark with a command like this: C:\ tshark.exe –r D:\cert.cap -d ber.syntax==,x509af -T pdml -V > res.txt ****Please, answer me, how can I decode x509 certificate in tshark and take all information about certificate in the output file. Please write example of a command for tshark for x509 certificate! It is very important for me – I`ve been trying to find answer during 3 weeks – but results are still next to zero! With a great regards, Dmitriy.**** asked 27 Dec '12, 02:14 pemolux |
One Answer:
The best you can do in tshark is to run one of these commands and parse the output.
The will contain all you are interested in. The 'fields' may differ in format and naming, but they are all there. BTW: What is your tshark version (tshark -v). You may need to upgrade to get the full functionality! UPDATE after some conversation, I figured out that a certificate file (test.cer) was loaded into Wireshark.
well that is a certificate and not a pcap file. Wireshark is absolutely the wrong tool to decode that file. What you need is openssl
You can download it from openssl.org (windows) your by installing it with our standard linux package manager (apt-get, yum. etc.) Regards answered 27 Dec '12, 02:41 Kurt Knochner ♦ edited 27 Dec '12, 23:27 showing 5 of 6 show 1 more comments |

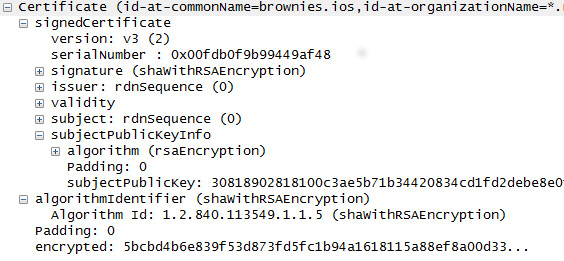
Thank you for your answe, Kurt! I use the latest stable version 1.8.4. I has tried your commands, but nothing new... I don't see any field names - only their values, as i see before.
strange, I do see all of them. They are indeed 'encoded', but easy to parse.
My example: SSL/TLS on google
Output of
tshark -nr google_ssl.pcap -R "ssl.handshake.certificates" -T pdmlOutput of
tshark -nr google_ssl.pcap -R "ssl.handshake.certificates" -VIf you look at that output, what are you missing?
Thanks! I don`t see values "name" - first values of "field". For example - container
field name="x509af.subjectPublicKeyInfo" showname="subjectPublicKeyInfo" size="162" pos="264" show="" value=""
i see like a
field name="" showname="" size="162" pos="264" show="" value=""
More the over, when try to parse certificate with your command, tshark don`t print any results. When I try to parse with option -d ber.syntax==,x509af, as I wrote before - it works, but do not print field names.
Could you try to parse your cert with my code sample? C:\ tshark.exe –r D:\cert.cap -d ber.syntax==,x509af -T pdml -V > res.txt
It`s very interest for me - will my problem repeat on your computer?
With Great Regards, Dmitriy
well, I do see them:
from:
http://pastebin.com/sfDfd7GKissuer:
<field name="x509af.issuer" showname="issuer: rdnSequence (0)" size="72" pos="55" show="0"validity:
<field name="x509af.validity" showname="validity" size="32" pos="127" show="" value=""not Before:
<field name="x509af.notBefore" showname="notBefore: utcTime (0)" size="15" pos="129" show="0" value="from:
http://pastebin.com/SWmscAX2issuer:
issuer: rdnSequence (0)validity:
You just need to extract the data of those fields. The format is different with
-Vand-T pdml, but the content is the same.So again, what is exactly missing in the output of tshark?
some questions:
The output is the same as with my command, just a lot more, as you did not restrict it to 'ssl.handshake.certificate'.
First of all, take my regards for your help!
My real situation descrided below:
1) I have a certificate - I post my real test certificate here (http://files.mail.ru/U9AG66)
2) If I change it`s extension to *.pcap, then open this file with WireShark, then make "Decode as... -> Certificate" - I will have good result, something like the first picture in my first post.
Now I want take the same results by tshark for this test.pcap file.
3) I start tshark with my command: C:\Program Files\Wireshark\tshark.exe –r D:\cert.pcap -d ber.syntax==,x509af -T pdml -V > res.txt
Here is the value of res.txt - http://pastebin.com/EUVcpjXd
4) I start tshark with your command: C:\Program Files\Wireshark\tshark.exe -nr D:\cert.pcap -R "ssl.handshake.certificates" -T pdml > res.txt
Here is the value of res.txt - http://pastebin.com/qdFDaNGX
As you can see the first sample have not field names. The second sample don`t have any decoded values at all. This is the real situation and I want find design for THIS situation. I could try to parse it without field names, but it will became a big problem
well that is a certificate and not a pcap file. Wireshark is absolutely the wrong tool to decode that file.
What you need is openssl
You can download it from openssl.org (windows) your by installing it with our standard linux package manager (apt-get, yum. etc.)
Regards
Kurt