How do I figure out why advanced ip scanner can see the ip address but I can't ping the ip address?
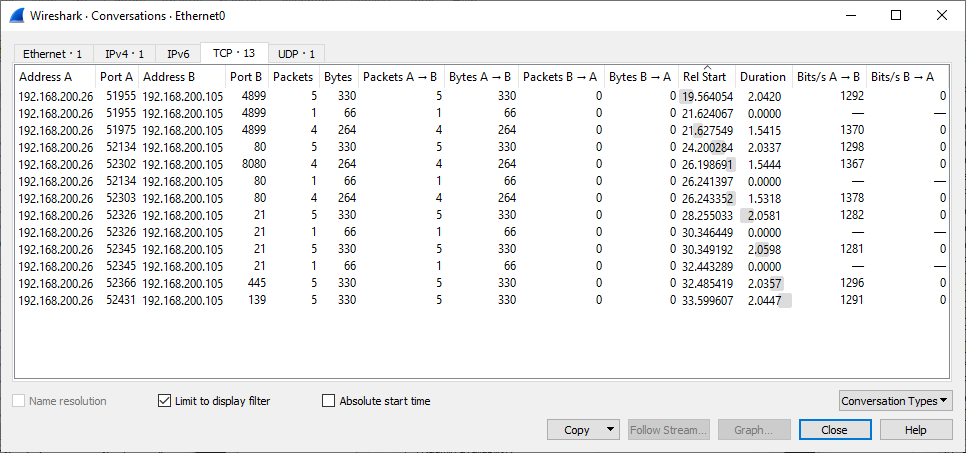
I've got a meraki firewall. My old camera network is on 192.168.1.0/24 network. On my PC, I am sitting with a 10.10.11.0/24 ip address, and I can ping the 192.168.1.254, which is the default gateway for the 192.168.1.0/24 network. However, I can't ping 192.168.1.108 which is the specific camera that is on the 192.168.1.0/24 network. Additionally, when I use advanced ip scanner, I can see the 192.168.1.108 as if it is online, but not yet pingable or reachable via HTTP. I am trying to do a packet capture, but really not sure how to capture or what expressions to use correctly to see maybe what is going on here??? Thoughts?
THank you,