encrypted trace question
I am working with a trace file captured between a smart home controller C4 and the client app.
Due to the lack of documentation for the communication protocol used I am trying to reverse engineer the commands from the existing trace, however it ?seems? to be encrypted with a self signed cert.
I have root access to the C4 controller (linux distro) and can easily obtain the self signed certificate .pem file.
Is my assumption about the trace being encrypted correct and if so how could I decrypt it using the private certificate obtained from the C4 controller?
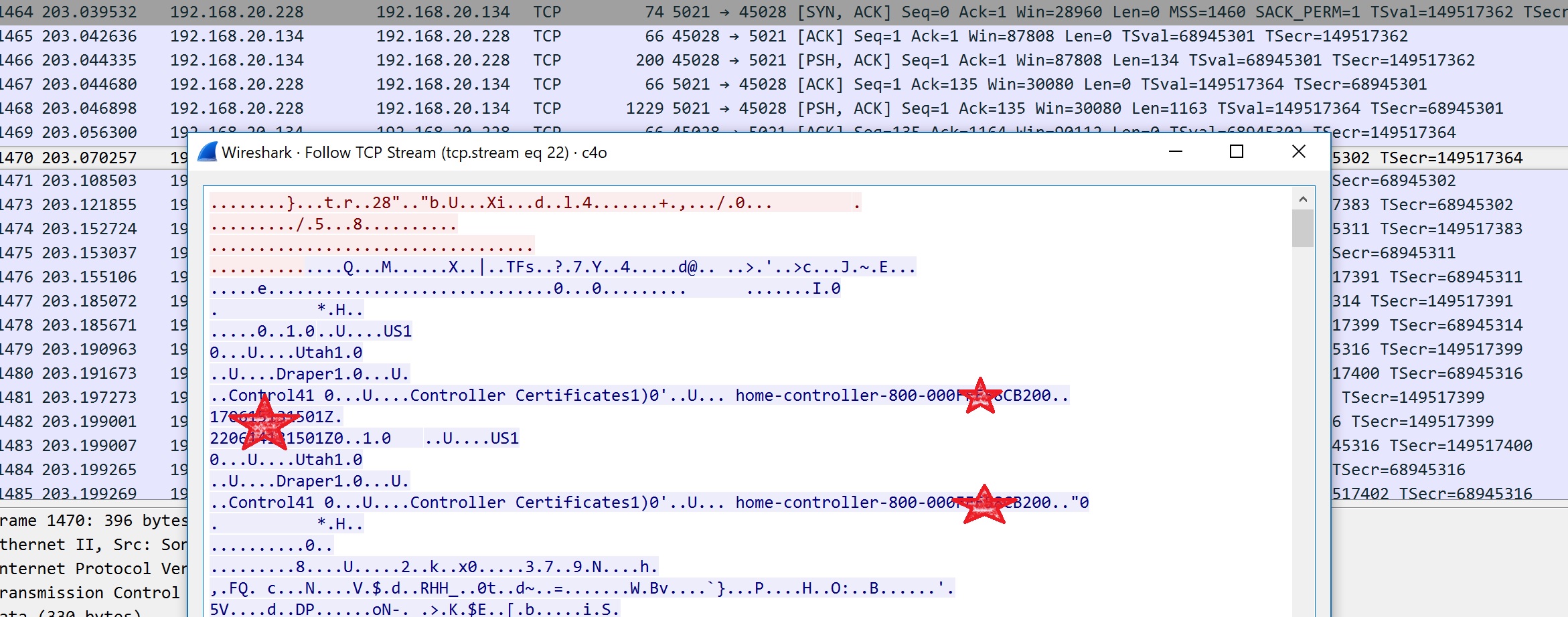
Some useful info here - http://pwn2ownnow.blogspot.com/
Thank you

