DCE/RPC Remote Procedure Call
Hey there,
I need some help of somebody who knows what's going on here. I researched a lot about DCE/RPC but there is not very much detailed information available on the web. Maybe somebody here can give me some information on the following capture:
(no need to get too deep into details, but if you like to you're welcome :)
*screenshot added:
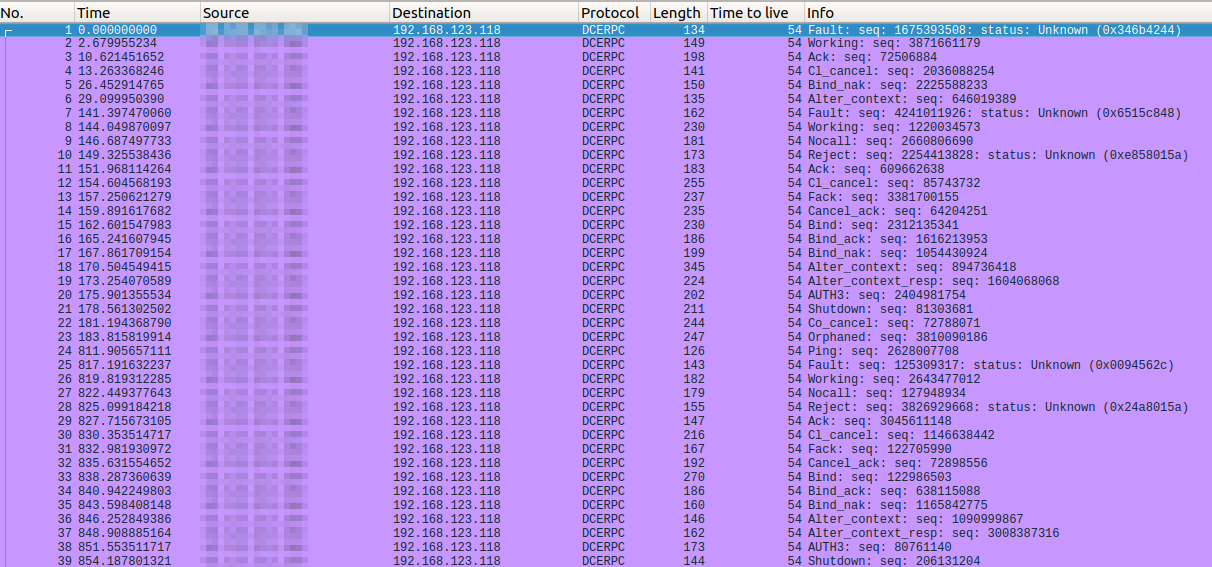
No. Time Source Destination Protocol Length Info
42 1495.384770518 *censored* 192.168.123.118 DCERPC 199 Ping: seq: 2274746402
Frame 42: 199 bytes on wire (1592 bits), 199 bytes captured (1592 bits) on interface 0
Linux cooked capture
Internet Protocol Version 4, Src: *censored*, Dst: 192.168.123.118
User Datagram Protocol, Src Port: 27015, Dst Port: 27005
Distributed Computing Environment / Remote Procedure Call (DCE/RPC) Ping, Seq: 2274746402, Serial: 32836, Frag: 11049, FragLen: 4152
No. Time Source Destination Protocol Length Info
43 1500.652624583 *censored* 192.168.123.118 DCERPC 213 Fault: seq: 2256318484: status: Unknown (0x05f6b8ce)
Frame 43: 213 bytes on wire (1704 bits), 213 bytes captured (1704 bits) on interface 0
Linux cooked capture
Internet Protocol Version 4, Src: *censored*, Dst: 192.168.123.118
User Datagram Protocol, Src Port: 27015, Dst Port: 27005
Distributed Computing Environment / Remote Procedure Call (DCE/RPC) Fault, Seq: 2256318484, Serial: 4, Frag: 7608, FragLen: 13051
No. Time Source Destination Protocol Length Info
44 1505.945566549 *censored* 192.168.123.118 DCERPC 295 Nocall: seq: 75521284
Frame 44: 295 bytes on wire (2360 bits), 295 bytes captured (2360 bits) on interface 0
Linux cooked capture
Internet Protocol Version 4, Src: *censored*, Dst: 192.168.123.118
User Datagram Protocol, Src Port: 27015, Dst Port: 27005
Distributed Computing Environment / Remote Procedure Call (DCE/RPC) Nocall, Seq: 75521284, Serial: 32900, Frag: 38104, FragLen: 260
No. Time Source Destination Protocol Length Info
45 1508.605860849 *censored* 192.168.123.118 DCERPC 273 Reject: seq: 997494462: status: Unknown (0x52ee2260)
Frame 45: 273 bytes on wire (2184 bits), 273 bytes captured (2184 bits) on interface 0
Linux cooked capture
Internet Protocol Version 4, Src: *censored*, Dst: 192.168.123.118
User Datagram Protocol, Src Port: 27015, Dst Port: 27005
Distributed Computing Environment / Remote Procedure Call (DCE/RPC) Reject, Seq: 997494462, Serial: 32836, Frag: 24606, FragLen: 42051
No. Time Source Destination Protocol Length Info
46 1511.268238242 *censored* 192.168.123.118 DCERPC 285 Ack: seq: 1399001244
Frame 46: 285 bytes on wire (2280 bits), 285 bytes captured (2280 bits) on interface 0
Linux cooked capture
Internet Protocol Version 4, Src: *censored*, Dst: 192.168.123.118
User Datagram Protocol, Src Port: 27015, Dst Port: 27005
Distributed Computing Environment / Remote Procedure Call (DCE/RPC) Ack, Seq: 1399001244, Serial: 32879, Frag: 7880, FragLen: 51480
No. Time Source Destination Protocol Length Info
47 1513.929900575 *censored* 192.168.123.118 DCERPC 302 Cl_cancel: seq: 3752523524
Frame 47: 302 bytes on wire (2416 bits), 302 bytes captured (2416 bits) on interface 0
Linux cooked capture
Internet Protocol Version 4, Src: *censored*, Dst: 192.168.123.118 ...
*hint: It might be an exploit via Steam-Client on these ports. It has nothing to do with a game or anything, and it appears randomly, unexpected. Maybe something non-public?