 | 1 | initial version |
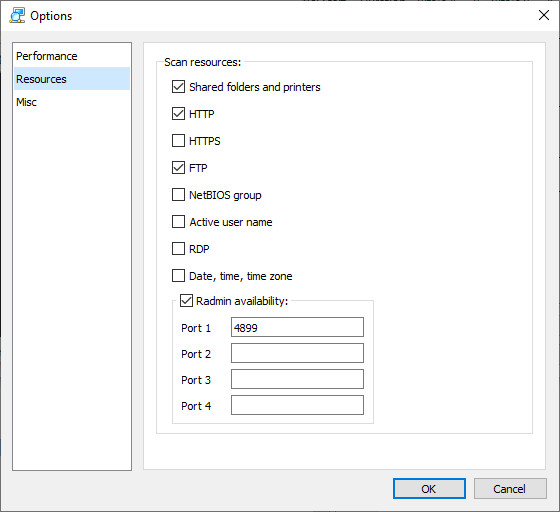
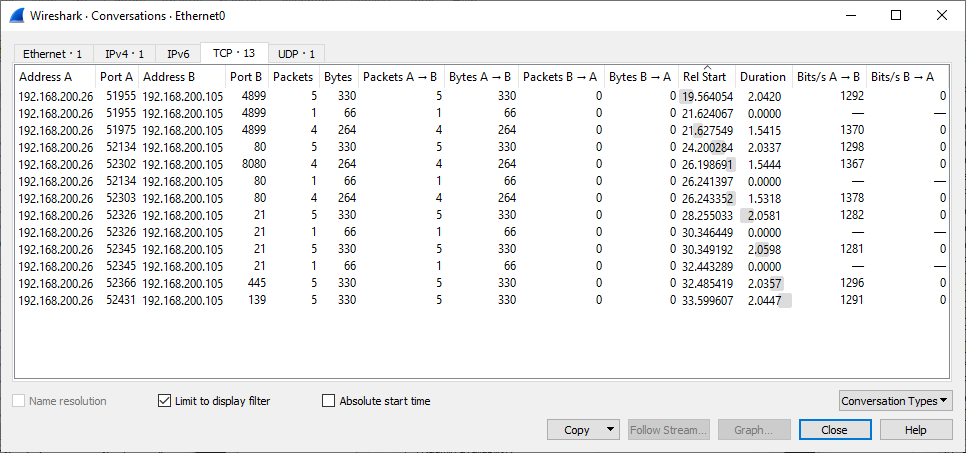
The application does network discovery with port scans not a ping (ICMP) sweep:
No. Time Source Destination Protocol Length Info 3212 19.564054 192.168.200.26 192.168.200.105 TCP 66 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3213 19.568213 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0 3350 20.076142 192.168.200.26 192.168.200.105 TCP 66 [TCP Retransmission] [TCP Port numbers reused] 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3357 20.080791 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0 3555 20.583165 192.168.200.26 192.168.200.105 TCP 66 [TCP Retransmission] [TCP Port numbers reused] 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3558 20.587136 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0 3627 21.098360 192.168.200.26 192.168.200.105 TCP 66 [TCP Retransmission] [TCP Port numbers reused] 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3629 21.103232 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0
If the firewall allows the outbound SYN and the camera responds that the port is not available (RST,ACK for this test device) then the application knows there exists a device with that IP address.
 | 2 | No.2 Revision |
The application does network discovery with port scans not a ping (ICMP) sweep:
No. Time Source DestinationProtocol LengthProto Len Info 3212 19.564054 192.168.200.26 192.168.200.105 TCP 66 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3213 19.568213 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0 3350 20.076142 192.168.200.26 192.168.200.105 TCP 66 [TCP Retransmission] [TCP Port numbers reused] 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3357 20.080791 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0 3555 20.583165 192.168.200.26 192.168.200.105 TCP 66 [TCP Retransmission] [TCP Port numbers reused] 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3558 20.587136 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0 3627 21.098360 192.168.200.26 192.168.200.105 TCP 66 [TCP Retransmission] [TCP Port numbers reused] 51955 → 4899 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1 3629 21.103232 192.168.200.105 192.168.200.26 TCP 60 4899 → 51955 [RST, ACK] Seq=1 Ack=1 Win=5840 Len=0
If the firewall allows the outbound SYN and the camera responds that the port is not available (RST,ACK for this test device) then the application knows there exists a device with that IP address.


